Teenage Cyberbullying
Origins
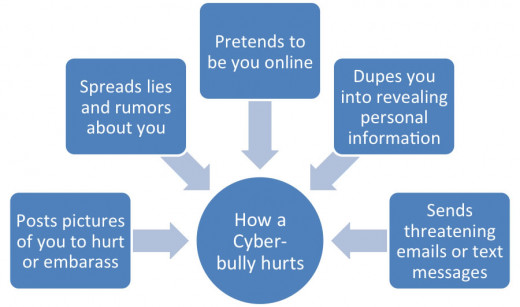
The legal definition of cyberbullying (n.d.) defines cyberbullying as any action that uses information and communication technologies to support deliberate, repeated, and hostile behavior by an individual or group that is intended to harm another or others. Cyberbullying arose from a combination of two main modes of mass communication, social media and text messaging. Cyberbullying first became a real issue for teenagers when social media sites, like Facebook, opened their gates to anyone over the age of 13. This expansion allowed anyone to join social media sites and opened the door for teenagers to create anonymous accounts using fake names. More recently social media itself has expanded to include anonymous social media apps like Yik Yak and Ask.fm; these apps allow teens to connect with other people near their location without anyone knowing who is on the other side of the app. These apps give bullies the opportunity to say anything they want without having to stand behind their own words (Perez, 2014).
Influences
There are two main points of view on teenage cyberbullying. One viewpoint is that cyberbullying is not a big deal and that offline bullying is the much bigger problem; people who share this viewpoint believe that the victim brings the bullying upon themselves by sharing their identities online and that stopping cyberbullying would only require stricter laws and for the victims to not place themselves up as bait (Landeros, 2013). The second main viewpoint is that cyberbullying is a serious problem that requires real solutions; this viewpoint is shared by 68% of teenagers according to DoSomething.org (n.d.). While both viewpoints agree that cyberbullying can be hurtful neither viewpoint realizes that there are actually three categories of people involved in cyberbullying: bullies, victims, and bully–victims (Mishna, Khoury-Kassabri, Gadalla, and Daciuk, 2012). According to Risk factors for involvement in cyber bullying: Victims, bullies and bully-victims (2012), bully–victims are teenagers who have experienced both sides of cyberbullying, meaning they have been both the victim and the bully at one point. Social media has recently begun to impact society’s views on cyberbullying through moderating and removing the accounts of cyberbullies and through serving as a place for information about cyberbullying to be shared. Social media has impacted my personal opinions about cyberbullying; social media has made me believe that social media sites need to have stricter forms of non-bullying rules. Social media users who engage in cyberbullying should be automatically banned.

Culture: High or Low
The issue of teenage cyberbullying is greatly influenced by teenage culture. Culture is defined as “the integrated and dynamic social system of behaviors, characteristics, customs, language, artifacts, and symbols that distinguish one social group from another” (Sterin, 2012, p. 461). The typical teenage culture includes certain social norms and behaviors such as: not reporting cyberbullying out of fear of losing online privileges, not believing adults can help stop cyberbullying, and thinking that it is best to stay quiet unless the cyberbullying became threatening (Agatston, Kowalski, and Limber, 2007).
Cyberbullying could be labeled as either high or low culture depending on the perspective of the person doing the labeling. Mass media revolution defines high cultures as “societies wherein both the producers and the consumers (the audience) of media content and the actual words, images, and stories heavily depend on a shared understanding of the context within which that media content is presented” (Sterin, 2012, p. 462). Cyberbullying could be seen as high culture because the message, media, or file that the cyberbully uses against his or her victim requires a shared understanding of the context. Both the cyberbully and the victim need to understand what is happening in order for the bullying to be occurring.
Mass media revolution defines low culture as “societies in which the media that are produced and consumed are generally straightforward” (Sterin, 2012, p. 463). Cyberbullying could easily be viewed as low culture because the bullying is straightforward; the cyberbully is using communication technologies in order to harm the victim through his or her typed words or shared pictures/files. Based on the definitions from the Mass media revolution I would personally view cyberbullying as more low culture than high culture as there is nothing sophisticated about cyberbullying; it does not involve any abstract ideas or contemporary social problems. It is merely about one person using communication technologies as a method to harm another person. The designation of low culture does to a certain extent affect societal attitudes about cyberbullying. For instance, many people tend to devalue the topic and blame the victim for sharing their identity online. This blaming the victim approach often leads to teenagers viewing cyberbullying as something to handle privately at home rather than through their school.
Career
Teenage cyberbullying is a topic that directly impacts the mass communication career of journalism. According to Van Der Haak, Parks, and Castells (2012) the current “digital environment in which journalists work has new facts are being unearthed daily; more audience feedback is being integrated, more voices are being heard, more diverse perspectives on the same news stories are being presented.” This new environment is what causes teenage cyberbullying to positively impact journalist. Journalists are now looking for new controversial topics to write about. Teenage cyberbullying is a topic that has society divided. This allows journalists to unearth new information on the topic and write about it from different viewpoints. Journalists will continue to benefit as the knowledge and research on cyberbullying increases. As more research studies are completed on the teenage cyberbullying, new viewpoints on the topic will be created which will allow journalists to pursue different avenues to write about. For instance, the creation of three categories of people involved in cyberbullying: bullies, victims, and bully–victims, have already given journalists the opportunity to pursue the viewpoints of teenagers who are both cyberbullies and victims (Mishna, Khoury-Kassabri, Gadalla, and Daciuk, 2012).

Trends and Future Directions
Teenage cyberbullying aligns with many current mass communication trends in social media. Teenage cyberbullying negatively uses the trend of creating anonymous social media accounts. Many teenagers use Yik Yak and Ask.fm; this trend of using anonymous accounts allows cyberbullies to bully teenagers without anyone knowing who the bully is; this anonymousness gives bullies the courage to do and say things that they never would if they had to stand behind their words and actions (Perez, 2014). As time continues to progress teenage cyberbullying will continue to evolve as will the technology and rules in place to prevent it. Currently, Facebook has created an online bullying prevention hub that provides users with ideas and assistance for cyberbullying problems on their site. More and more social media sites will begin to take steps similar to Facebook to provide their users with cyberbullying assistance. It is also likely that social media sites may begin to hire moderators to remove cyberbullies from their sites. These changes will cause mass communication to evolve in order to protect social media users from cyberbullies.
References
Agatston, P. W., Kowalski, R., & Limber, S. (2007). Students’ perspectives on cyber bullying. Journal of Adolescent Health, 41(6), S59-S60. doi:10.1016/j.jadohealth.2007.09.003
DoSomething.org. (n.d.). 11 Facts About Cyber Bullying. Retrieved April 11, 2015, from https://www.dosomething.org/facts/11-facts-about-cyber-bullying
Landeros, R. (2013, April 14). Opposing Side: Cyber Bullying. Retrieved April 11, 2015, from http://cbrozz.blogspot.com/2013/04/opposing-side-cyber-bullying.html
Legal Definition of Cyberbullying. (n.d.). Retrieved April 11, 2015, from http://encyclopedia.thefreedictionary.com/cyberbullying
Mishna, F., Khoury-Kassabri, M., Gadalla, T., & Daciuk, J. (2012). Risk factors for involvement in cyber bullying: Victims, bullies and bully-victims. Children and Youth Services
Review, 34(1), 63-70. doi:10.1016/j.childyouth.2011.08.032
Perez, S. (2014, December 18). Few Winners In Anonymous Social Networking, And Secret's Not One Of Them. Retrieved April 11, 2015, from http://techcrunch.com/2014/12/18/few-winners-in-anonymous-social-networking-and-secrets-not-one-of-them/
Van Der Haak, B., Parks, M., & Castells, M. (2012). The future of journalism: Networked journalism. (special feature). International Journal of Communication (Online), 2923.








